Your pages and your site are exposed to became the container of malicious code, code somebody placed in your page without your approval. You include code from outside, because you need advertising and tracking codes, but these elements are out of your control. Malvertising and bad tracking codes are ready to take control of your pages.
Such front end code (JavaScript, Flash, etc) can manipulate the content of your page, read data present in the form users are editing, collect these information and send somewhere else. Taking advantage of vulnerabilities present in browser plugins, this code injected in your site pages could even be able to install specific malware into user PC.
Being a front end manipulation often site managers have no visibility on what is happening, only the end user browser is affected.
But when emails, credit card numbers and other personal information are moved to someone else without the explicit approval of the user due to malicious code in your pages, this is a legal responsibility of site owner and he can be persecuted even if he is a victim as the end user.
IMPORTANT: the term “malvertising” is mostly referred to an advertising banner able to install a malicious software, called malware, in the user PC. Here we will focus on advertising able to interact with your page, stealing data such as username, password, credit card numbers.
How this malicious code can be placed in your pages:
1) because of your developers or content editors: for a mistake or an infected pc, somebody allowed to change your site place some malicious code inside your pages. It is a quite rare, but the examples of infected pc involuntary able to included external malicious JavaScript are present in security literature.
2) because the page is not well designed it can be exposed to cross site scripting: somebody can inject runtime JavaScript code using a specifically designed url. So I can send by email a link to a regular official page of yours with special parameters and when your page is opened, it contains some malicious code. Check pages against cross site scripting is quite simple, just use some standard penetration test application.
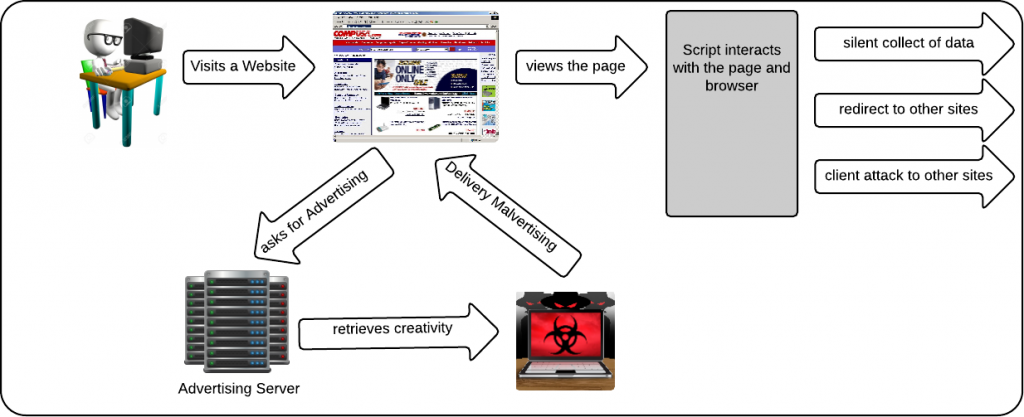
3) because the page include some tag like advertising, tracking code, external content: these tags are usually a chain of “include” very complex and the owner of the site is never able to control what is really coming inside his pages. You include a tag provided by your adv server then, when executed, this piece of code include other scripts coming from other sources and so on. Some adv servers are quite strict in control, but the biggest part are quite easy to be tricked. This malicious advertising is called malvertising, and it is one of the most critical point in secure your pages.
We will focus on this 3rd case: insecure advertising, insecure tracking codes, not controlled external content.
What malvertising and bad tracking codes can do:
In the worse cases a marvertising is able to install a malware directly into the client PC just when an advertising banner appears on the page, without any active action done by the user. This is usually done taking advantage of vulnerabilities of browser plugin. In this case only a good antivirus and a good antimalware can help the client PC to be protected (we will speak in the future more in deep regarding these issues).
What an antivirus / antimalware can not block is the interaction between script in your pages and your page content. As described before, these front end codes included from outside can:
1) they can read all the parameters arriving to your page and send them away
2) they can read all parameters, text fields, passwords, credits card numbers present in the page and send them away
3) they can redirect your page to any other site
4) they can change the content of your page
5) they can use your page, and your customers, as attach vehicle to other site
What can you do to protect your site from malvertising and bad tracking codes?
Assume we review the code before any deploy and we protect our page from cross site scripting. This means we need to protect our pages only from malicious code coming through advertising, tracking code or any included content. These kind of components can not be secured by design or with architectural solutions and, in the real world, we need them even if they are a possible risk. Protecting your site depends on your business models and your sources of revenue.
Regarding Tracking code and advertising there are 3 main approaches:
1) avoid them
If you can avoid advertising and 3rd part tracking codes in your site, this for sure will make your life safer. Not only for the risk of malware code, but for the risk your page is not loaded correctly by the final users, or part of them, because the source of this advertising or tracking codes is not available, is performing under expectation, has any error, is not compatible with some browsers, and so on. This does not mean to remove these stuff from all the pages of your site, maybe from the critical pages (login, profile pages, payment pages,…)
2) isolate them
Iframe with sandbox is a good solution to isolate piece of code/content and block any chance of bad code to look around your page. It does not work with all the code. Google analytics needs to be in your page, it does not work as supposed if located inside an iframes. The same for some advertising tag and tracking code. Multi location advertising (multiple advertising in the same page) need to be coordinated to avoid competitor advertising in the same page, and to be coordinate they need to see each other. These can’t be isolated with iframe sandbox. Take a look to this page about HTML5 sandbox. You can start implementing Content Security Policy as detailed described in this post about Content Security Policy.
Pay attention: Some malvertising are able to install viruses and trojan software in the client PC, just because they appeared in the webpage. If you are able to isolate the advertising in a sandbox, this can block the malicious script to interact with your page, not to install malware.
3) audit them
This is the most time consuming activity. Pay attention to any script/include you put in your page. Take a look to the source of this code. Maybe there are sources you relay upon more than other. Allow external includes only when you are sure of the content and you are sure this external part is not including something else. Better if you download this 3rd part code, save it in your site and include it from your repository, just to be sure nobody will change it without your approval. But it must be always the same. Most of the times this approach is not compatible with tracking codes and advertising, because the script changes every call or the call itself is used to track the data, like getting the transparent pixel.
Content Security Policy
Recent browsers implement CSP, Content Security Policy, so now you are able to define some rules to restrict the behavior of external content based. CSP provides a method for website developers to define approved origins of content that browsers should be allowed to load on that website page. This policy is applied to content types like JavaScript, CSS, HTML frames, web workers, fonts, images, embeddable objects such as Java applets, ActiveX, audio and video files, and other HTML5 features.
As often happened in the past, there is not shared a standard. Content security Policy are implemented in different browser with different mechanisms.
| Response Header | IExplorer | Firefox | Chrome | Safari |
Content-Security-Policy |
no | from v.40 | from v.43 | from v.8 |
X-Content-Security-Policy - deprecated |
from v.10 partial | no | no | no |
X-Webkit-CSP - deprecated |
no | from v.4 to v.22 | no | no |
| details from: caniuse.com/ContentSecurityPolicy | ||||
Content-Security-Policy should be the official standard response header to implement CSP, even if at this moment it is not supported by Microsoft Internet Explorer.
Final thoughts
Security does not come for free. Protect your critical pages, like registration, payment, login, removing any advertising or tracking codes. Use only the ones from reliable sources with a defined content.
[…] 4: Theft of credential Target are the user credentials. Multiple techniques from “man in the middle” to “social engineering”. A particular interest in the subject regarding external code injection. More details in Protect your site from Malvertising, Bad tracking and malicious iframe contents […]